Intro
In the ever-evolving realm of cloud infrastructure, orchestrating secure and scalable environments across multiple AWS accounts presents a unique set of challenges. This technical blog explores the significance of adopting a multi-account architecture in AWS, delves into the hurdles associated with multi-account deployments, and outlines a strategic solution utilizing Terraform, AWS CodePipeline, and Infrastructure as Code (IaC) principles. Additionally, we’ll provide a concrete example of deploying an EKS cluster in one account and an ALB in another, shedding light on the rationale behind their separation.
The Significance of Multi-Account Architecture in AWS
Adopting a multi-account architecture in AWS provides numerous advantages. It allows organizations to separate workloads, applications, and development environments, providing a natural isolation that enhances security and compliance. Each account becomes a logical unit, enabling independent management of resources, permissions, and billing. Furthermore, a multi-account architecture supports scalability, agility, and streamlined resource allocation, making it a key strategic choice for organizations with diverse and evolving cloud infrastructure needs.
The Challenge: Multi-Account Deployments with Terraform
Deploying resources across diverse AWS accounts becomes a formidable challenge, especially when leveraging Terraform for Infrastructure as Code. Generally, when using Terraform to deploy and manage Amazon AWS resources, the Terraform project will be working with AWS resources in only a single AWS Account. The intricacies include cross-account references, limited support for specific AWS Organizations features, and the imperative need for granular permissions. These challenges necessitate a thoughtful solution to seamlessly manage configurations spanning multiple accounts. Organizations aspiring to deploy resources across different AWS accounts encounter hurdles that demand a strategic solution.
Terraform Providers: A Strategic Solution
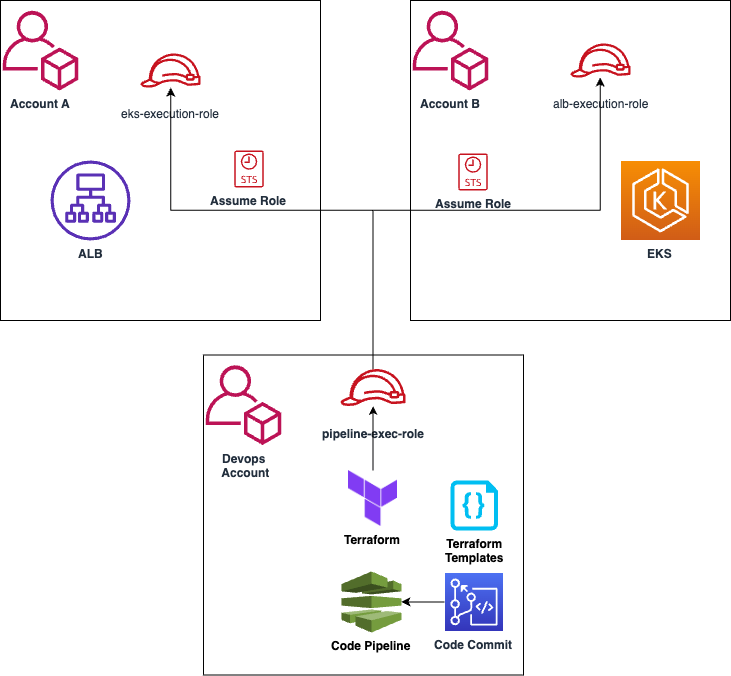
The crux of the solution lies in the strategic use of Terraform providers. By creating distinct provider configurations, roles are assumed in specific AWS accounts. This approach enables secure cross-account resource orchestration, effectively addressing isolation and permission complexities.
Example: Deploying EKS in Account A and ALB in Account B
Consider a scenario where an organization needs to deploy an EKS cluster in a production AWS account (Account A) and an ALB to manage ingress traffic in a separate ingress AWS account (Account B). This separation serves a dual purpose: it ensures isolation, reducing the blast radius of security incidents, and it adheres to the AWS Well-Architected Framework’s best practices, enhancing fault tolerance and scalability.
Reasons for Separation:
- Security Isolation: Placing critical production workloads, like an EKS cluster, in a dedicated account minimizes the impact of security incidents or vulnerabilities.
- Scalability and Fault Tolerance: Separating the EKS cluster and the ALB into different accounts allows each to scale independently, enhancing fault tolerance and avoiding resource contention.
The provided Terraform code exemplifies the orchestration of resources across multiple AWS accounts using Terraform providers, roles, and modules. Let’s break down the key components. Here, two AWS providers are defined, each with a distinct alias (“eks” and “alb”). These providers are configured with different regions and IAM roles. The assume_role block specifies the IAM role that Terraform assumes when interacting with AWS.
provider "aws" { alias = "eks" region = "us-west-2" # EKS cluster region assume_role { role_arn = "arn:aws:iam::PRODUCTION_ACCOUNT_ID:role/eks-cluster-role" } }provider "aws" { alias = "alb" region = "us-east-1" # ALB ingress region assume_role { role_arn = "arn:aws:iam::INGRESS_ACCOUNT_ID:role/alb-ingress-role" } }
Centralized IAM Role: Ensuring Security and Audibility
Within the deployment account, a dedicated IAM role plays a crucial role during the deployment process. Trusted by both EKS and ALB IAM roles in their respective accounts, this approach establishes secure, centralized control. IAM roles adhere to the principle of least privilege, ensuring granular permissions and enabling a transparent and auditable deployment process.
The code includes an EKS (Amazon Elastic Kubernetes Service) cluster module. It is configured to use the AWS provider with the “eks” alias.
module "eks_cluster" {
source = "terraform-aws-modules/eks/aws"
cluster_name = "production-cluster"
providers = {
aws = aws.eks
}
}Deploying an AWS Application Load Balancer (ALB):
resource "aws_lb" "ingress_alb" {
provider = aws.alb
name = "ingress-alb"
internal = false
load_balancer_type = "application"
security_group_ids = [aws_security_group.ingress_sg.id]
# Other ALB configurations
}Centralized Deployment Control
To streamline the deployment process and overcome cross-account challenges, AWS CodePipeline takes center stage. Configured in a centralized deployment account, CodePipeline orchestrates the release workflow, encompassing source, build, and deploy stages. The deployment stage triggers Terraform scripts, ensuring a centralized and automated deployment pathway. AWS CodePipeline serves as the linchpin in this deployment strategy. In the centralized deployment account, a CodePipeline pipeline is configured to pull the Terraform scripts from a version control system. The pipeline orchestrates the entire deployment, from source code changes to the actual provisioning of resources. Importantly, it’s designed to work seamlessly across multiple accounts, thanks to the IAM roles assumed by Terraform providers.
Benefits of the Integrated Solution
- Isolation: Resources, exemplified by the EKS cluster and ALB, can be deployed in separate AWS accounts, ensuring isolation and minimizing security risks.
- Centralized Control: CodePipeline acts as a control tower, providing visibility and control over the entire deployment process, streamlining management.
- Least Privilege: IAM roles strictly adhere to the principle of least privilege, reducing the risk of unnecessary permissions and enhancing security.
- Audibility: The established trusted relationships between IAM roles support a transparent and auditable deployment process, critical for compliance and security standards.
Conclusion Achieving Efficiency and Security
This comprehensive solution showcases how the strategic integration of Terraform providers, AWS CodePipeline, and Infrastructure as Code (IaC) principles offers a robust answer to the challenges of deploying in multiple AWS accounts. By addressing the complexities of cross-account configurations, organizations can efficiently deploy and manage resources, achieving a balance between security, scalability, and centralized control in their AWS infrastructure.
Leave a Reply